This encryption method was loosely inspired by the 2016 science fiction movie “Arrival,” in which the alien species uses a visual language composed of circular ink blots to form words and sentences. Since I am a fan of polar coordinates, a mathematical system often used to describe circular motions in orbital mechanics, I decided to use them to encode texts. Specifically, letters are represented by radial lines, whereas numbers and symbols are represented by arcs around the image center. This creates unique line plots, which contain all the information of the encoded plaintexts while also achieving a unique aesthetic.
Before briefly explaining polar coordinates, you first have to understand Cartesian coordinates, the gold standard that has been used to torture calculus and algebra students for millennia. In Cartesian coordinates, a 2D position can be described by the horizontal value x and the vertical value y. However, in polar coordinates, 2D positions are described by the polar angle φ and the radius ρ. The two coordinate systems can be converted into one another using the following equations:
x = ρ · cos(φ)
y = ρ · sin(φ)
This makes polar coordinates more suitable to describe orbital mechanics. For example, a circular motion around a specific point only requires the polar angle φ to be changed while the radius ρ remains constant. Conversely, for a radial motion (similar to gravitation), the polar angle φ is constant while the radius ρ is changed. Typically, in Cartesian coordinates both x and y would need to change for either of these motion types, which leads to more complicated math than needed. On a sidenote, I also used polar coordinates for the particle movement in my projects AntNation, DEEP FL0YD, and Brushing MBS. But enough of mechanics for now and on to the actual cipher.
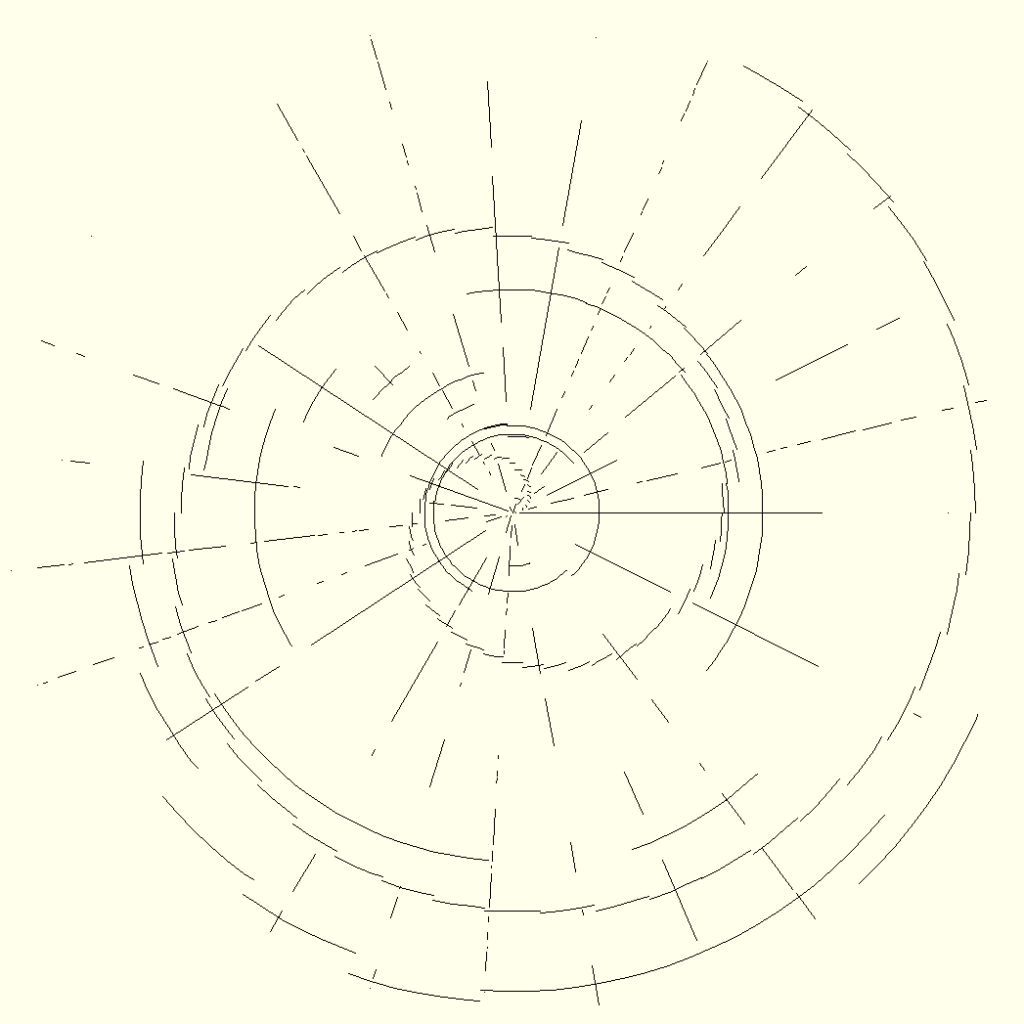
First, the letters of the alphabet are associated with equally spaced angles φ, beginning at 3 o’clock and rotating counterclockwise, as is customary in mathematics. You can see this in the image below. The encoded message is read beginning in the center of the image and working your way outward in a radial direction. Whenever a certain letter appears in the plaintext, a line is drawn that only stops when the letter appears a second time or when the message is over. Technically, the lines are not necessary and drawing single pixels would suffice, but I found lines more visually pleasing. In a nutshell, one would need to draw a bunch of concentric circles whose radii increase one pixel at a time and check where one of the 26 lines begins or ends on a circle, then write down the corresponding letter.
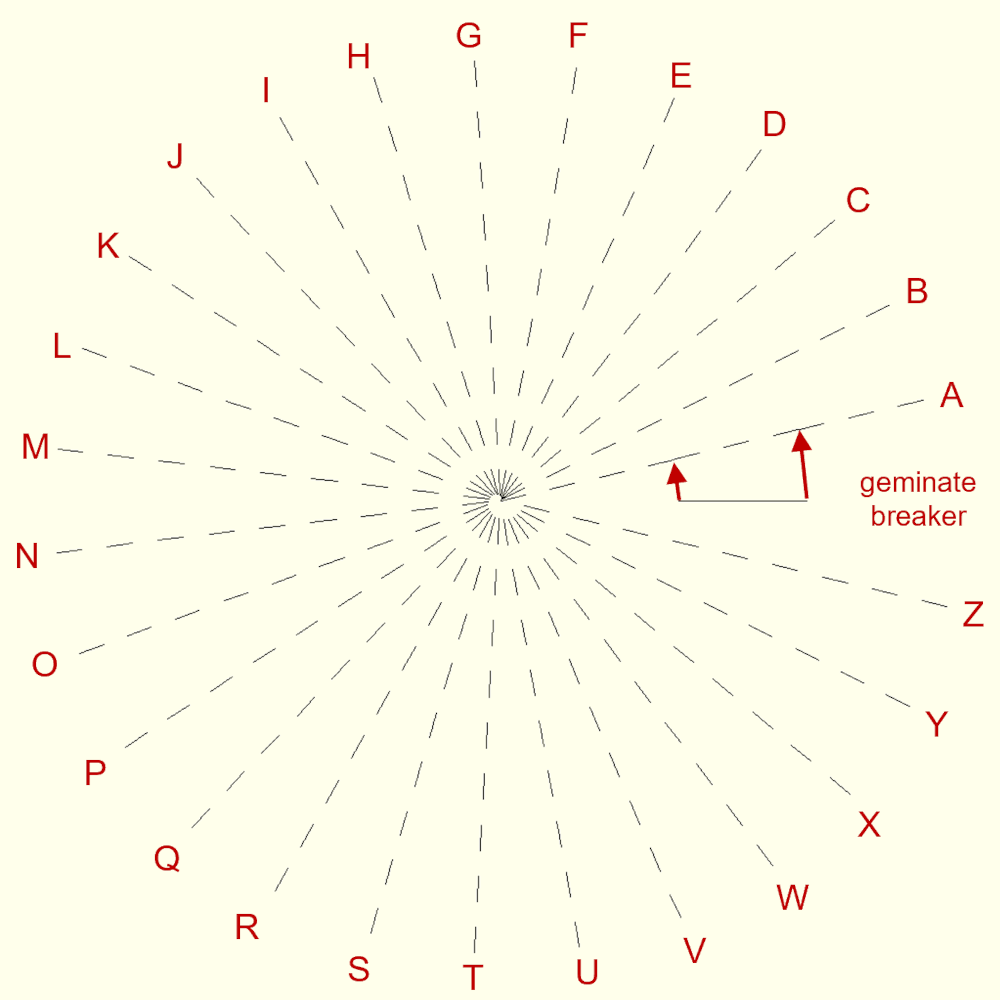
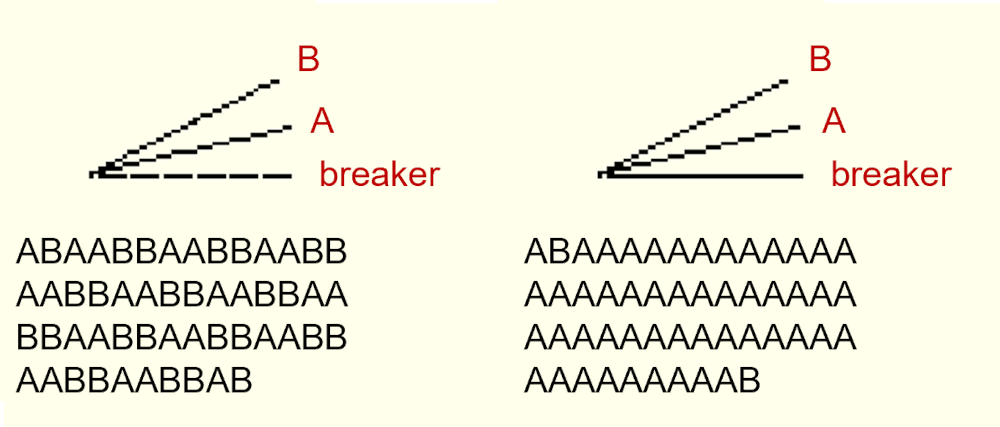
You might notice that I added an additional line, which I named “geminate breaker” for lack of a better word. Actually, a geminate is a linguistic term to describe consonant lengthening by repeating a letter, such as the word “letter” containing two T’s. But in a broader sense, I refer to any double letters because they could mess up the cipher. Particularly, they could lead to two collinear lines that touch each other and thus might be mistaken for a single line. Hence, a virtual letter, the geminate breaker, is inserted to indicate where that is the case. As an example, compare the two messages in the image below. They are quite different, the second one containing a lot more A’s than B’s – but note that their respective radial lines look the same. However, the geminate breaker lines clearly distinguish them by indicating problematic AA and BB combinations. (To be precise, the lines for A and B are slightly dissimilar, which has to do with the way they are drawn in the Python module pygame and less so with the math.)
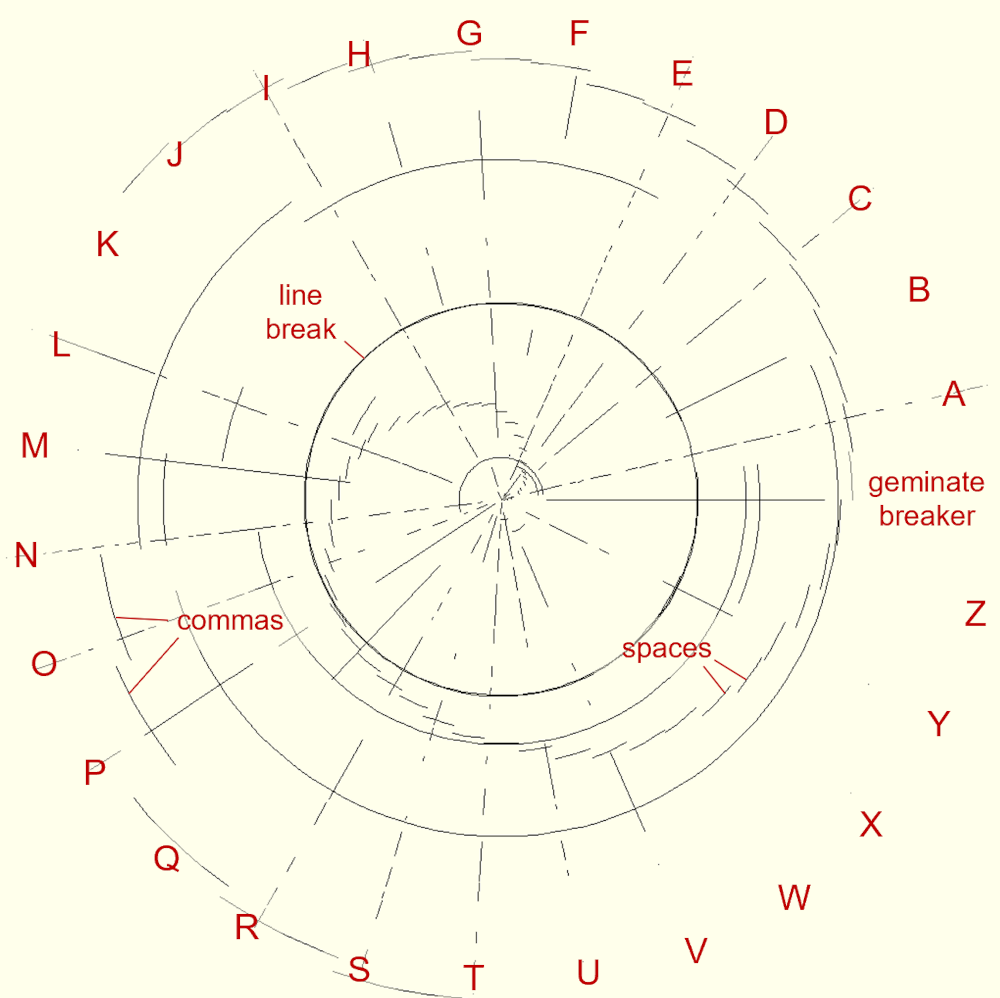
Next, I overlayed the image with arcs that represent all the numbers, symbols, and other important text structuring elements, such as space characters, line breaks \n, and tabulators \t. They are evaluated in the following order: ,.-–—'"!?:;0123456789()/\&#%@[]{}*+=§$~^\t\n\r (in case you missed it, there is a leading space character). The further to the right a symbol stands in this sequence, the longer the respective arc is, meaning that the carriage return \r will draw a full circle (360°), whereas the common space character will only draw 1/44 of a full circle (8.18°), a comma 2/44 (16.36°), a period 3/44 (24.55°), and so on.
Just because I found it most aesthetic, I let one arc begin at the same angle at which the last arc ended, forming distinct spiral patterns for each symbol. Perhaps all my elaborations become clearer when you look at the image below, which contains a representative part from my text “Oatcrusher and Old Evil.”
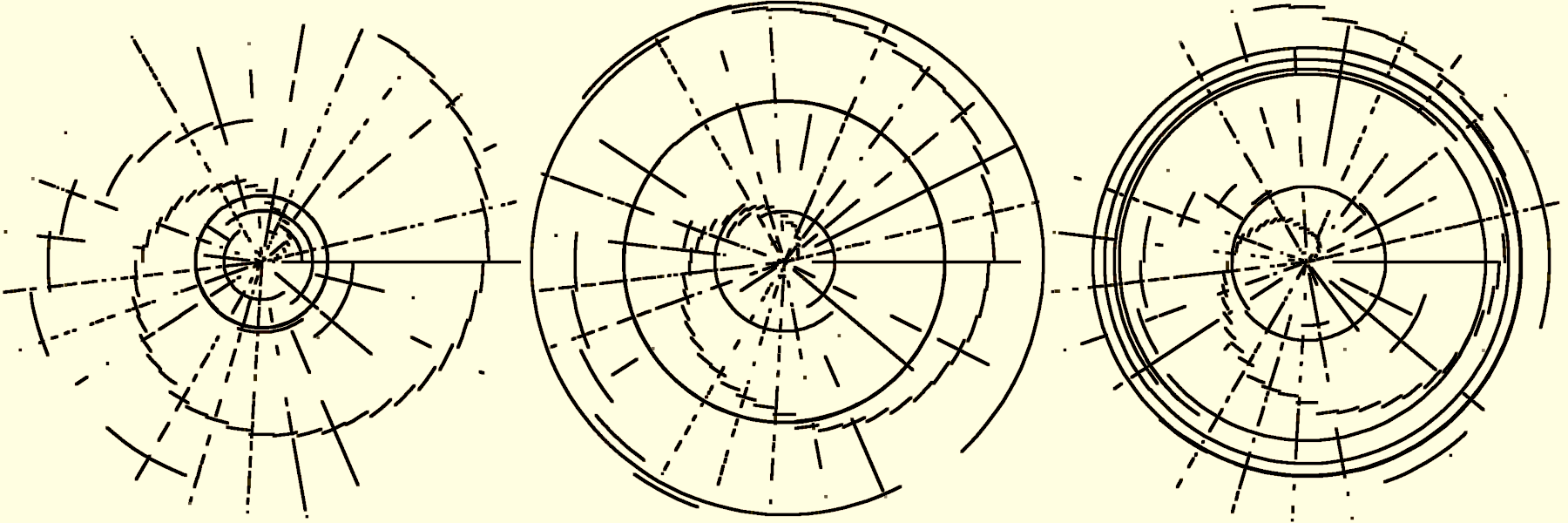
If you are the keen observer that I think you are, you might already have noticed one disadvantage of Polar Cipher: the image resolution depends greatly on the length of the plaintext N. To be precise, the resolution is always 2 · N – 1 due to the concentric nature of the cipher. Consequently, I split the plaintext into chunks of equal size (the last chunk almost always being smaller because it contains the remaining characters). Groups of 512 characters seem ideal because the resulting image resolution of 1023 × 1023 pixels is still manageable. It is worth mentioning that the image file size is increased quadratically with the message length, which does not scale well. The ciphertext can then be depicted as a sequence of images, which are showcased in the animated GIF below. As a matter of fact, it encodes the text of this very post. How meta!
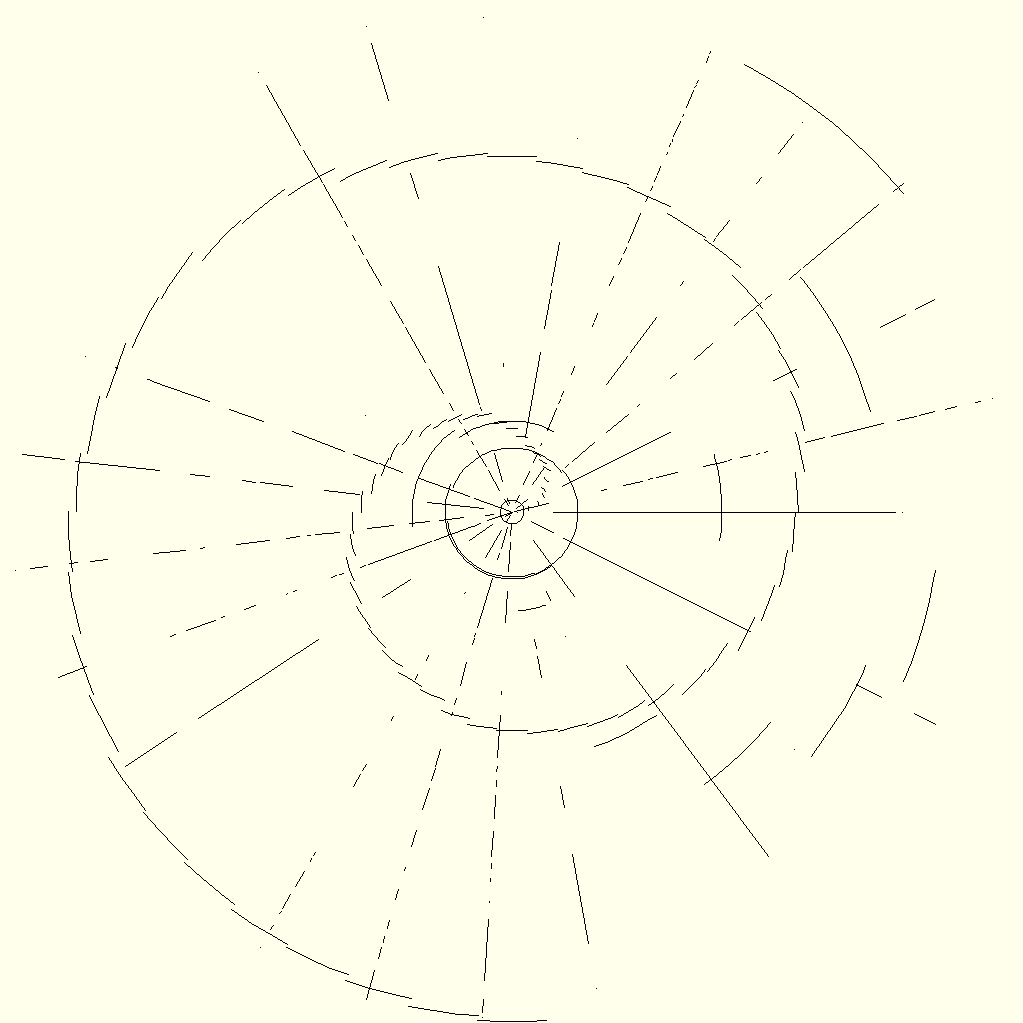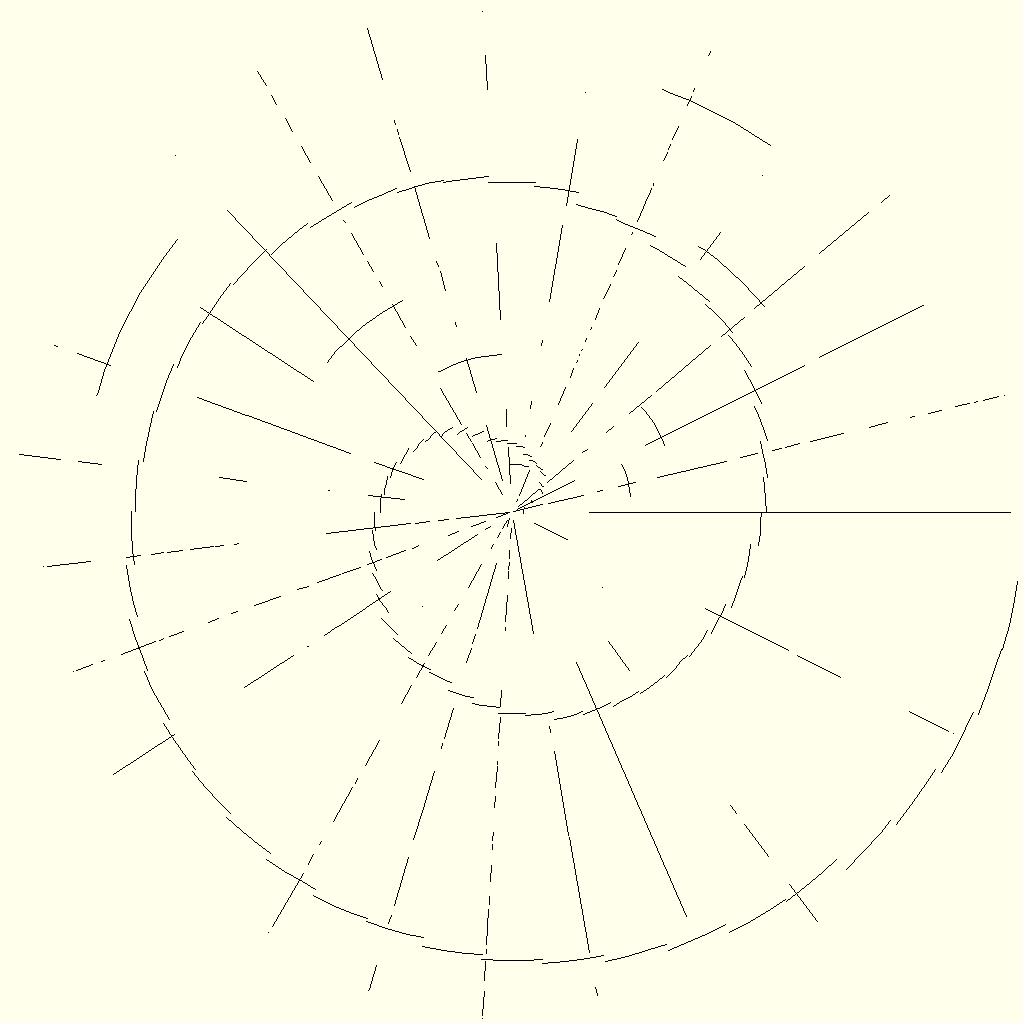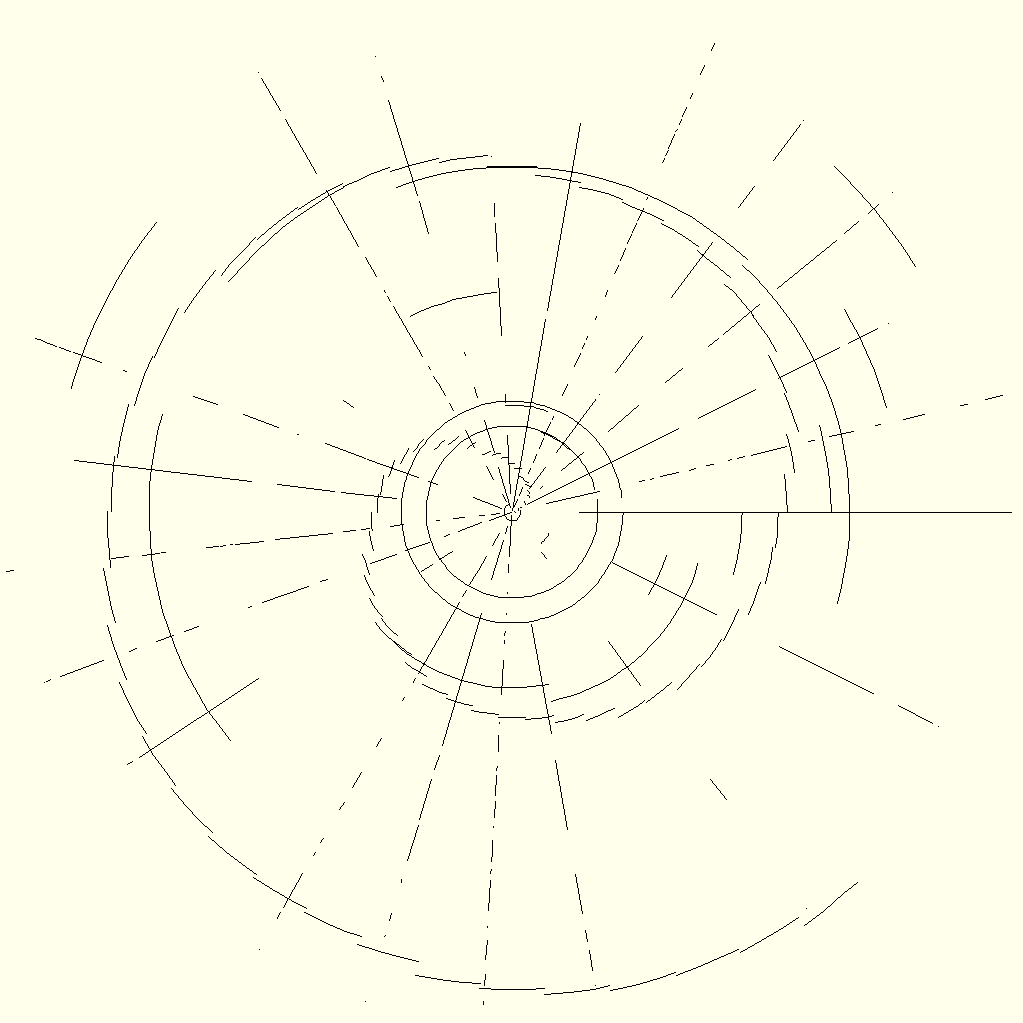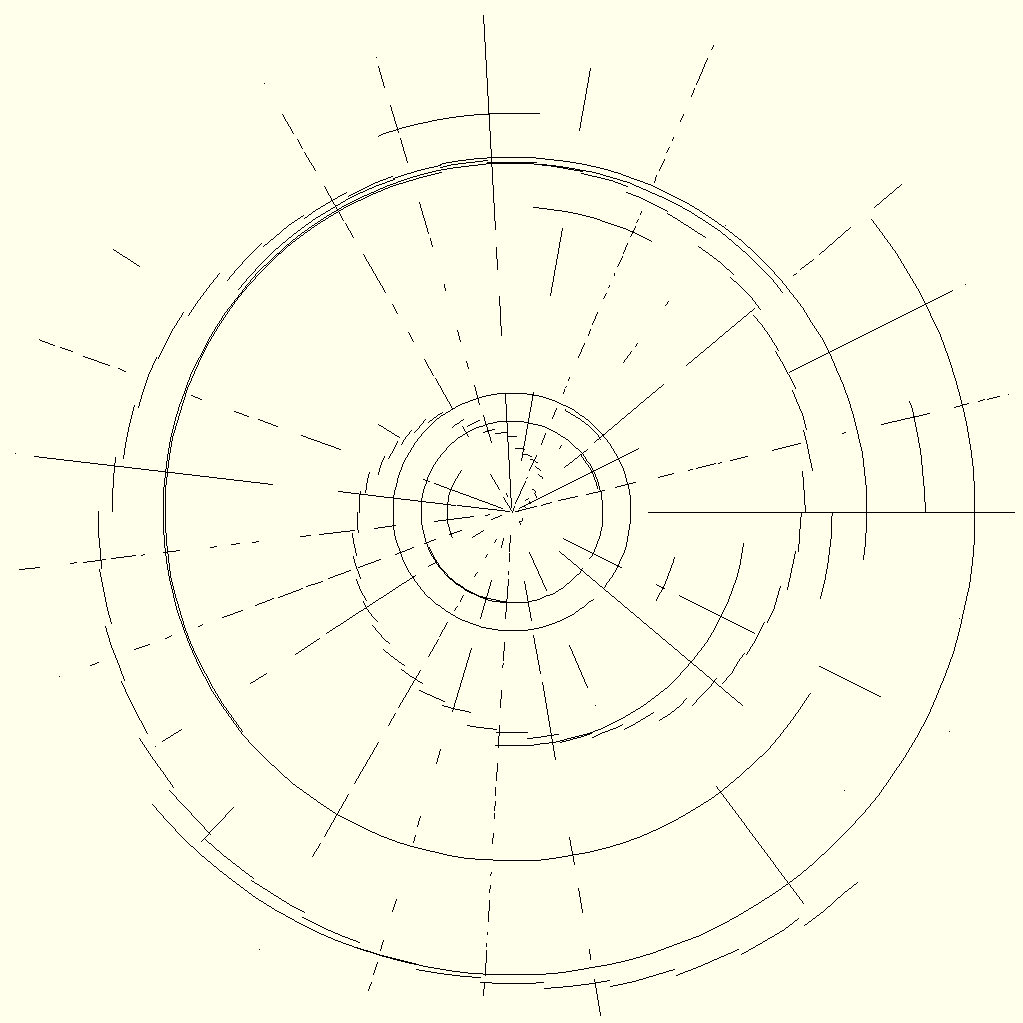
By now, you have learned the essentials of how the cipher works. This would be a good moment to make a confession: while the encryption of plaintexts is easy to perform, the decryption is not. To be frank, I wrote the code that creates the cipher images in a single afternoon, but I lack the coding and image processing skills to convert them back into plaintext. Or rather, I would get there eventually, but it would take a huge effort to follow up on such a minute idea.
Therefore, I will leave Polar Cipher as what it is right now: an obscure, esoteric cryptographic art project. It is not trying to be an efficient graphical encoding format for text, such as QR codes or simple bar codes. However, feel free to commence right where I stopped if you are up to the task. I suppose that the cipher images contain all the information necessary for decryption, but until it has been done there is no way to know for certain whether the cipher has major design flaws.
To motivate you, the images below contain a particularly juicy message that I would not be comfortable sharing as plaintext.
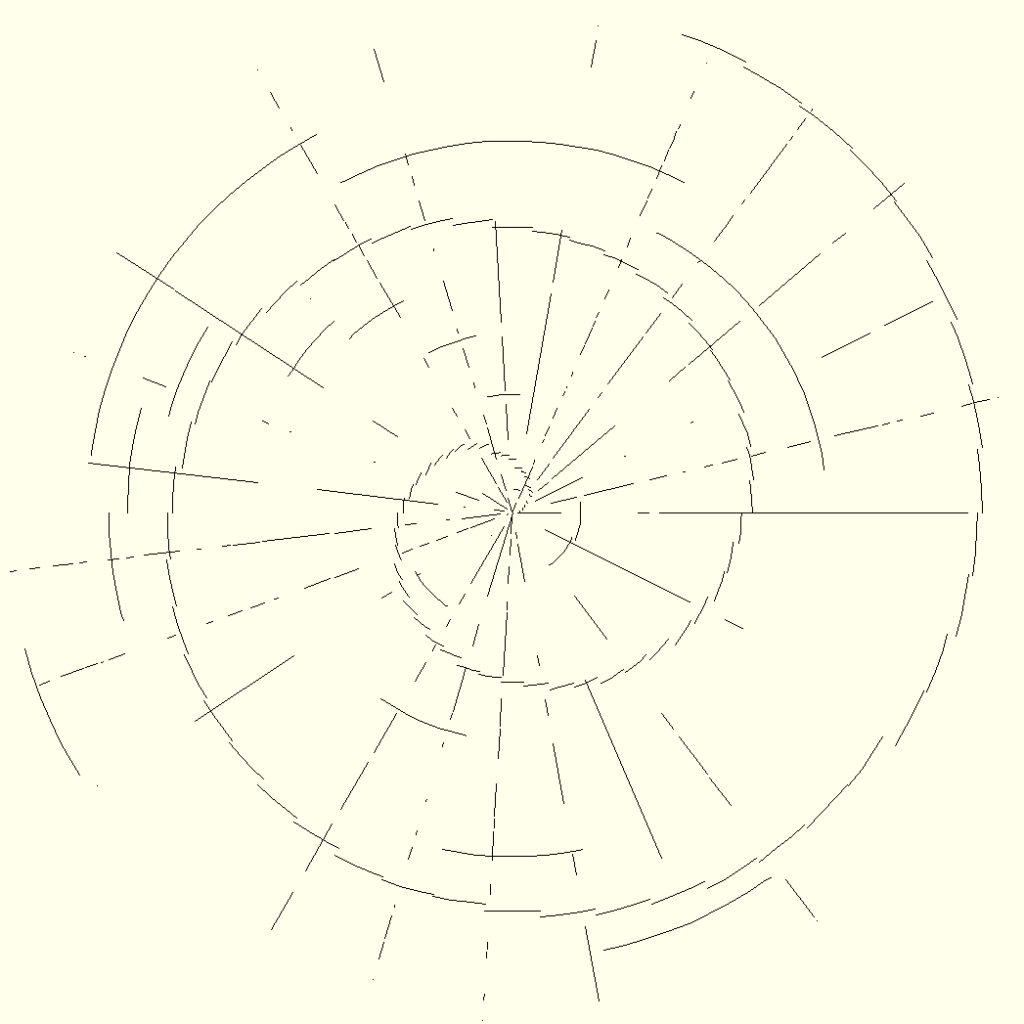


Leave a Reply