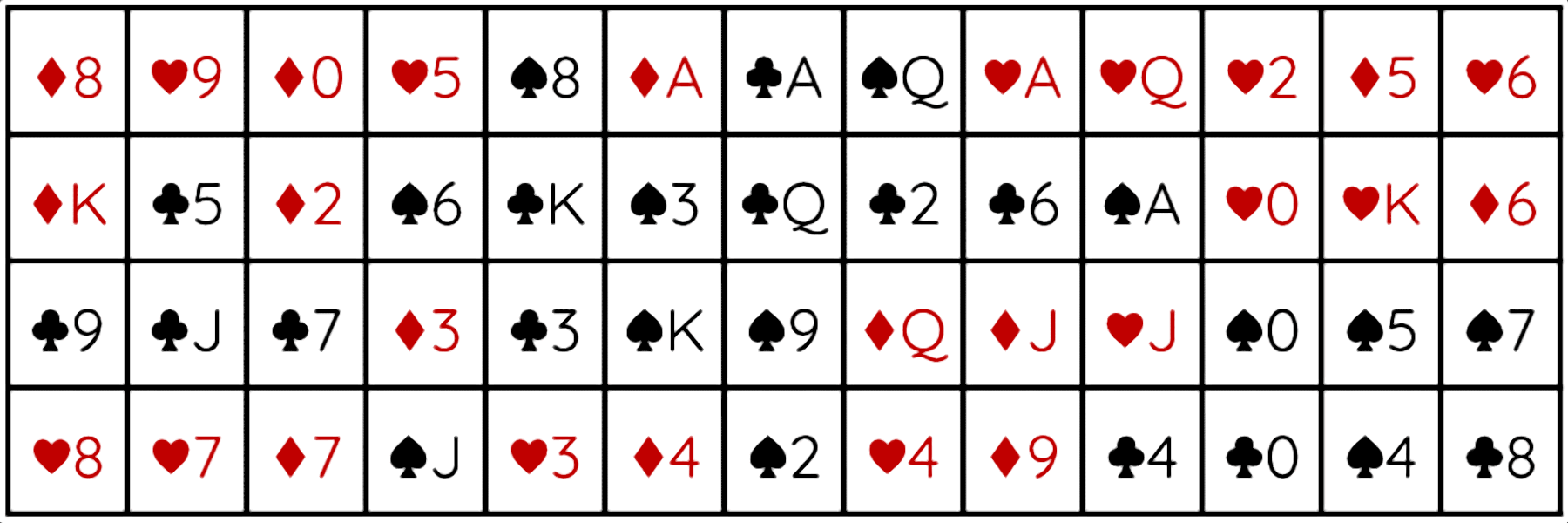
This encryption method is based on a standard deck of 52 cards and can be used with pen and paper or a computer. The default order of the deck is clubs (♣), diamonds (♦), hearts (♥), spades (♠). Within each suit, the cards are ordered as ace (A), two (2), three (3), four (4), five (5), six (6), seven (7), eight (8), nine (9), ten (0), jack (J), queen (Q), king (K).

The key is obtained by randomly shuffling the deck, resulting in roughly 8 · 1067 permutations.

Plain text
“I built you a shrine behind a secret door. I’m gonna make you mine because I need you more. But something is amiss and that thing is you.”
Encryption
To achieve maximum obfuscation, the cipher consists of two steps: rearrangement and substitution. First, the plaintext is cleared of all spaces and punctuation, divided into chunks of 52 letters, and padded with random letters if necessary. Each chunk is then written to a 4 × 13 grid, which represents the shuffled deck, and rearranged to match the sorted deck.

Subsequently, in the substitution step, each letter is shifted by the value of the corresponding key card, similar to a Caesar or Vigenère cipher. The card values can comply with any card game, but I sort them from ace = 1 to king = 13 to give each card a different value. Additionally, black suits (♣ & ♠) shift in a positive direction, while red suits (♦ & ♥) shift in a negative direction, for example: Y & ♦8 = 25 – 8 = 17 = Q.

QEEDVCUNQBCDYGJBEUFMKSVCVCDDLRLEVOQHQFLSHAPKXPHISUSWAKYBUROKGWGPYRTEZLWTGTBYZONOAFXBCRRBCJLGAUDXNPORWKRAEXOIXTMBELVGDOHQPOQAQQEVGHWRQJHKYWJNSFXIDNEDQBBNMIIA
Decryption
Decryption follows the same steps in reverse order. With proper practice, one only needs to hold onto an inconspicuous card deck and ensure that it is not accidentally shuffled.
IBUILTYOUASHRINEBEHINDASECRETDOORIMGONNAMAKEYOUMINEBECAUSEINEEDYOUMOREBUTSOMETHINGISAMISSANDTHATTHINGISYOUBJOKADQMNHFYHWRYBPRJUNFZUFSCJVYQGPRYJKHXYFRKUIPJOF
Unfortunately, this encryption method has very low key sensitivity. That means, if two key cards are swapped, the corresponding plaintext letters are swapped in the same fashion. This makes the cipher very succeptible to hill climbing attacks, for which the key is incrementally changed while the deciphered text is scanned for an increasing number of letter groups that resemble actual words.


Leave a Reply